There are multiple legal aspects of the ICIF that warrant attention. We discuss here two aspects in particular: (1) establishing suitable legal agreements among ISE participants to support operational use of the ABA for information sharing missions, and (2) intellectual property rights related to the various components of the ICIF.
Legal Agreements for Operational Use of the ABA
As we have discussed, to meet the needs of the ISE communities, the Assertion-Based Architecture (ABA) must perform many functions related to assertions. For example:
- It must enable the expression of detailed policy requirements across many use cases and sub-communities.
- It must enable the assessment of participating agencies against those requirements.
- It must enable the results of those assessments to be shared, trusted, and relied upon for operational trust decisions.
But in addition, and perhaps most importantly, it must provide a legal framework so that disputes can be resolved in the event that things go wrong.
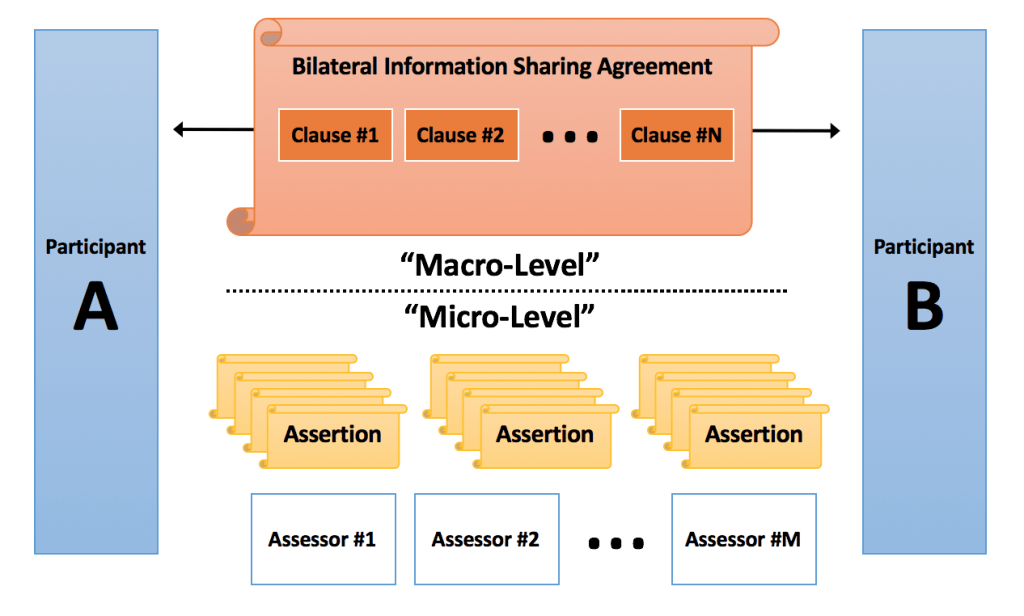
As the following diagram depicts, within the ABA, there are two legal frameworks of note. One framework relates to the “macro-level” information sharing agreements between partner agencies, and the other framework relates to the “micro-level” issuance and usage of actual assertions. We discuss each framework below.
ABA Macro-Level and Micro-Level Legal Frameworks
Macro-Level Legal Agreement via the ABC
As we discuss, the ABA includes an Information Sharing Agreement Builder Capability (ABC) that facilitates the development of componentized, machine-readable legal agreements to support specific information sharing use cases where a legal agreement is required. Despite existing in a perhaps unusual machine-readable format, the agreements produced by the ABC are typical bilateral or multi-party legal contracts that any attorney would recognize. So this particular aspect of the ABA is not unusual from a legal standpoint. The diagram above illustrates a typical (in this case bilateral) macro-level information sharing agreement between two ISE participants. The agreement contains a series of clauses that describe the terms of the agreement and the promises or guarantees that each party makes to the other party.
Micro-Level Legal Agreement via Assertions
As indicated by the diagram above, the micro-level legal framework within the ABA is richer and more complex than the macro-level framework. At the micro-level, ISE participants take advantage of many assertions they have received through self-assessment and/or from one or more third-party assessors, and they use those assertions to demonstrate proof-of-satisfaction for specific trust requirements imposed by their partner agencies.
The legal framework at the micro-level is richer than the macro-level framework, for the following reasons:
- While the legal agreements at the macro-level explicitly name their participants, the agreements at the micro-level must be more flexible. In other words, once an assessor issues an assertion to an agency, that agency can leverage the assertion across many use cases with many partner agencies. But the identities of all the partner agencies that will rely upon the assertion are not known at the time the assertion is issued.
- The number of agreements that exist at the macro-level is relatively small. Typically, an agency would execute only a handful of agreements — perhaps one agreement per information sharing use case or mission. But at the micro-level, the number of legal agreements can be vast, as each assertion carries its own explicit legal agreement.
- Agreements at the macro-level can have as few as two participants, and each party to the agreement must legally execute the agreement. In contrast, the legal agreement surrounding an assertion is inherently a three-party agreement, because it always includes (1) the assertion assessor, (2) the assertion recipient, and (3) the assertion relying party. And since any given assertion may have many relying parties that rely upon it, there can be many separate legal agreements in force for each assertion. In other words, legal agreements for assertions are in some aspects much more subtle and complex than macro-level information sharing agreements.
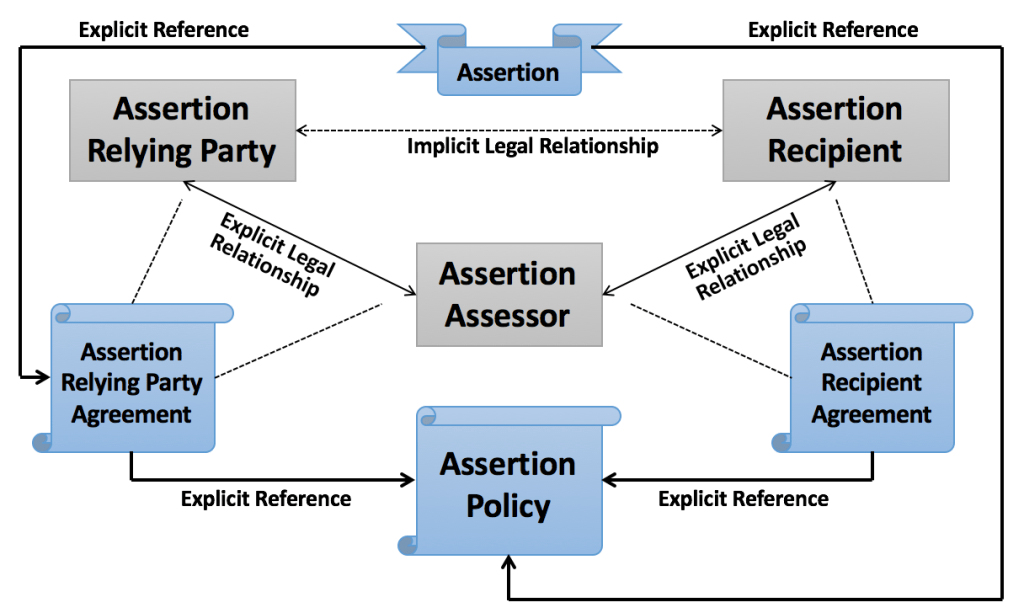
To support and accommodate the inherent richness of legal agreement that accompanies assertions, the ABA includes a novel Assertion Legal Framework, which is depicted below.
The Assertion Legal Framework
Within this framework, each assertion issued by an assessor is subject to an assertion recipient agreement, a standard two-party contract that establishes an explicit legal agreement between the assessor and the recipient. The agreement incorporates an assertion policy by reference.
When an assertion relying party chooses to rely upon an assertion, the relying party must enter into an assertion relying party agreement with the assessor. This agreement is also a two-party contract, but it is a “clickwrap” or “clickthrough” agreement rather than a “standard” agreement. This agreement also incorporates the assertion policy by reference.
Note that even though the purpose of an assertion is to provide a basis for trust between the assertion recipient and assertion relying party, the legal framework does not establish an explicit legal relationship between these two entities. Instead, it establishes separate explicit legal relationships between each entity and a third party, the assessor, which issued the assertion.
ICIF Intellectual Property Rights
Another important ICIF-related legal topic that may be of concern to ISE stakeholders is intellectual property rights (IPR). From an IPR perspective, there are three prominent components of the ICIF that deserve note here:
- ICIF Source Policies and Normative Tech Specs;
- The ICIF’s ABA Framework; and
- Published ABA Artifacts.
We address each one below.
ICIF Source Policies and Normative Technical Specifications
As discussed here, with respect to policies and tech specs, the ICIF seeks not to invent anew, but rather to leverage and reuse existing artifacts that are already in place and commonly used and accepted by ISE stakeholders. Thus, for example, the ICIF would not require the development of new security policy guidance, provided that existing security policy guidance (e.g., the FBI CJIS Security Policy or NIST SP 800-53) is acceptable to participants. Similarly, the ICIF would not require the development of a new technical specification for federated identity, as long as participants deem it acceptable to leverage the existing SAML 2 or OpenID Connect standards. As these policies and specs are typically developed and published outside the scope of the ICIF, the ICIF obviously makes no IPR claims upon them. From an ICIF perspective, the following two guidelines apply to these types of artifacts:
- Any externally developed source artifact leveraged by the ICIF is subject to the IPR restrictions assigned to that artifact by its original publisher or owner.
- While ISE stakeholders are permitted to use whatever external source policies and tech specs best enable them to achieve their mission goals, stakeholders are encouraged, whenever possible, to choose and implement policies and tech specs that are freely and openly available for download, review, and use without royalties or other usage-related restrictions.
The ICIF’s ABA Framework
As discussed here, the ABA’s core framework is implemented using the trustmark framework (TMF), which was developed by the Georgia Tech Research Institute under a U.S. government grant. The ongoing maturation and lifecycle management of the TMF is handled under the Trustmark Initiative. The TMF is freely available for use by the entire ISE community.
Published ABA Artifacts
As we have explored in detail through our discussion of the various ABA capabilities, there are many types of artifacts that can be published within the ABA, including:
- Assertion Definitions (ADs);
- Assertion Profiles (APs);
- Assertions; and
- Information Sharing Agreements (ISAs) and ISA Templates.
IPR impacts each of these artifact types as follows:
ADs and APs: As we discuss here, the Assertion Authoring and Publishing Capability (AAPC) enables any ISE stakeholder group to develop and publish its own ADs and APs. Stakeholders are free to assign IPR restrictions to their published AD and AP artifacts, but are encouraged to make these artifacts freely available for wide reuse by other stakeholders and stakeholder groups throughout the ISE.
Assertions: As we discuss here, the Assertion Assessor Capability (AAC) enables the issuance and publication of assertion artifacts based on the results of their assessments, whether self-assessed or externally (third-party) assessed. The AAC empowers the entity performing the assessment (i.e., the assessor) to issue and publish assertions based on that assessment, and therefore, the assessor is is free to impose any IPR restrictions on the assertions that it publishes. But assessors are encouraged to make their published assertions freely available for wide reuse, to provide maximum benefit across the ISE.
ISAs and ISA Templates: As we discuss here, the Information Sharing Agreement Builder Capability (ABC) enables the development and publication of ISA template artifacts representing the set of agreed-upon legal terms and conditions for various missions and use cases (including entire agreement templates and template fragments — e.g., agreement roles, technical and policy requirements, legal terms-and-conditions clauses, etc.), as well as actual ISA artifacts representing executed legal agreements. The ISA permits developers of ISAs and ISA templates to choose whether to publish them or keep them private. Publishers of ISA templates and template fragments are encouraged to make their published artifacts freely available for wide reuse, to provide maximum benefit across the ISE.
[previous] [next]