As we discuss on the introduction page, the Information Sharing and Safeguarding (IS&S) Core Interoperability Framework (ICIF) is designed to help Information Sharing Environment (ISE) stakeholders achieve information interoperability within all of their missions through a cost-effective, agile, decentralized, and scalable platform. But what exactly is the ICIF?
The ICIF may be best understood as a new “layer” that sits atop the existing “stack” of Internet-based communication infrastructure and provides new capabilities related to semantic interoperability and trust. The diagram below depicts the ICIF within this context.
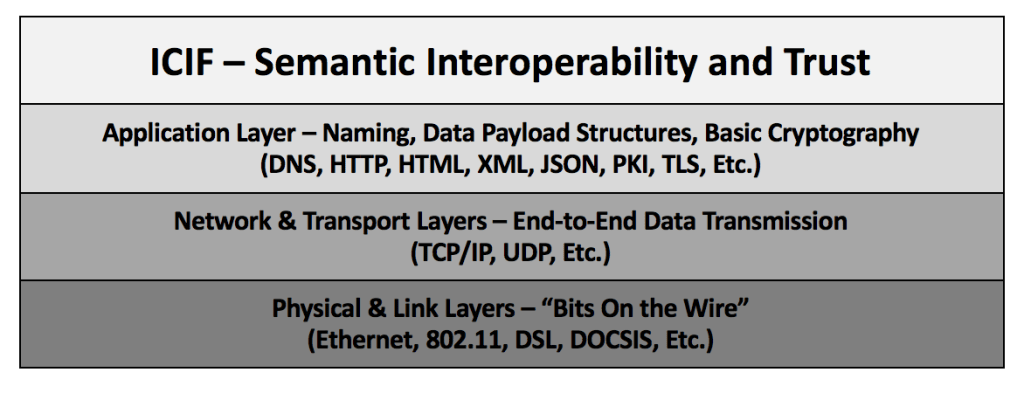
ICIF in the Context of the Internet Layers Architecture
As indicated by the diagram, the functionality typically associated with the “Internet” can be divided into multiple layers, in which each layer builds upon the functionality offered by the layer(s) beneath it and provides new functionality to the layer(s) above it. From bottom to top, the diagram above includes the following traditional network layers.
- The “Physical Layer” and “Link Layer” are concerned with leveraging the properties of basic physics to send “bits on the wire” — where the “wire” may be an actual copper wire, fiber optic cable, or wireless spectrum. Protocol standards that operate at this layer include Ethernet, IEEE 802.11, DSL, DOCSIS, LTE, and others.
- The “Network Layer” and “Transport Layer” take advantage of the basic services provided by the lower layers to provide “end-to-end” data transmission from one device to another. The most popular protocol standard at this layer of the stack is TCP/IP, although other protocols (e.g., UDP) also exist at this layer.
- The “Application Layer” provides additional services and capabilities beyond end-to-end data transmission. These include human-understandable naming (via DNS), application-layer protocol semantics (via HTTP), data payload formats (via XML and JSON), data payload display semantics (via HTML), basic cryptographic primitives such as encrypted channels (via PKI and TLS), and others.
As the diagram indicates, we can think of the ICIF within this larger framework as yet another layer of the stack. It takes advantage of the lower layers to provide higher-level services related to semantic interoperability and trust. In essence, the ICIF helps to promote greater trust and interoperability among ISE stakeholders by providing increased transparency and coordination regarding stakeholders’ conformance to semantically important policy and technical rules. This includes rules about security, privacy, identity assurance, data payload formats and semantics, protocol standards and profiles, and other topics.
As noted on the introduction page, the ICIF includes two primary components. The first is a collection of pre-existing, externally published and vetted technical and policy sources. These include NIST SP 800-53, NIST SP 800-63, the FBI CJIS Security Policy, FICAM, NIEM, SAML, OpenID Connect, GML, NIEM, and others. Together, these sources provide a core library of interoperability and trust requirements that ISE participants can leverage. The second component is an Assertion-Based Architecture (ABA): a technical framework that enables the wide-scale use of lightweight digital assertions to convey trusted statements about ISE participants’ compliance with rules derived from the external technical and policy sources. The primary purpose of the ABA is to acknowledge the inherent heterogeneity that exists among ISE stakeholders with respect to implementation, conformance, and compliance with these technical and policy sources, and enable ISE stakeholders to demonstrate their alignment with appropriate parts of the whole in a format that is componentized and reusable across many use cases with many ISE partner agencies.
[previous] [next]