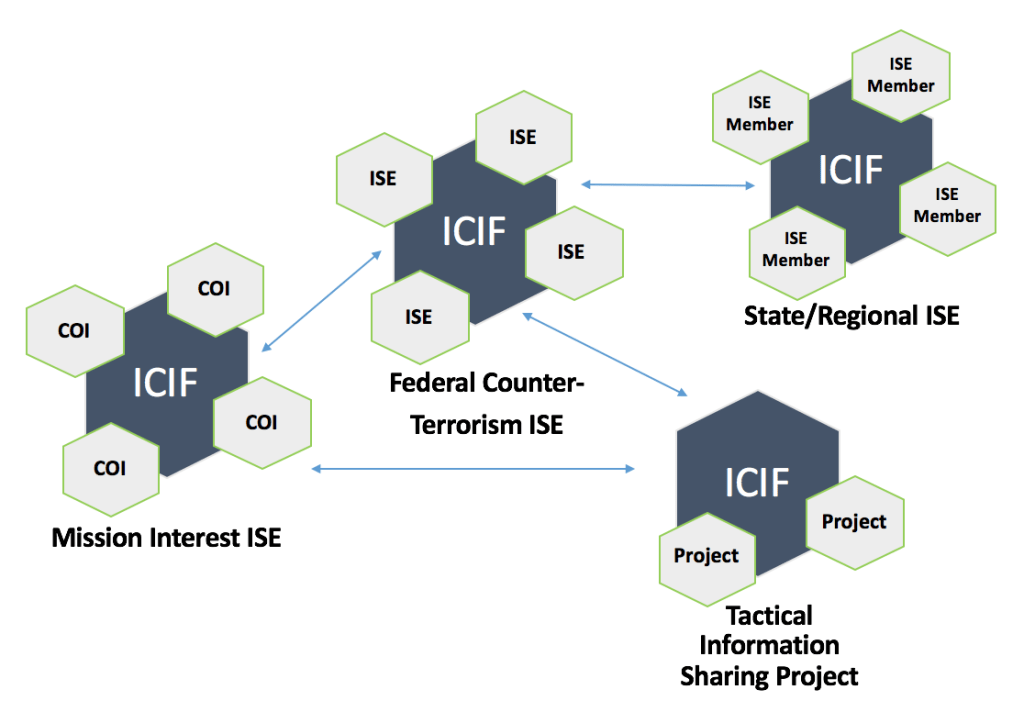
The ICIF is a powerful and flexible platform that can offer compelling benefits to many different types of Information Sharing and Safeguarding (IS&S) stakeholders. On this page, we identify four seemingly unique perspectives on the IS&S challenge, and we then describe why the ICIF can provide significant value for each case. The four perspectives that we cover are:
- The Federal Counter-Terrorism (CT) ISE;
- State/Regional (S/R) ISEs;
- Mission Interest ISEs; and
- Tactical ISEs.
Four Unique Perspectives
The Federal Counter-Terrorism (CT) ISE
As per the Intelligence Reform and Terrorism Prevention Act of 2004 (IRTPA), “the ISE” is that set of IT and communications capabilities, policies, and other resources that organizations employ to share information in order to counter terrorism and the proliferation of weapons of mass destruction (WMD) at the domestic nexus of national security and public safety. While the law refers to “the ISE” as if it were a unified whole, it is in fact merely the conceptual capstone of a web of other ISEs — both formal and informal — that exist at the federal, regional, state, local, and tribal-territorial (FSLTT) levels of government, most of which have primary purposes other than counterterrorism/WMD.
The Federal CT ISE is distributed, both horizontally and vertically. Because information of CT and counter-WMD interest to the federal government can originate at any level, the ability to rapidly exchange such information between and across the levels dictates that each node in the resulting de facto national network (ISE) adhere to some degree of standardization, coordination, and trust.
There is only one Federal CT ISE. It is expected to conduct and coordinate information sharing for CT and WMD purposes not only at the federal level, but between the federal government and the subordinate levels mentioned previously.
State/Regional (S/R) ISEs
As its name implies, a S/R ISE is established at, and serves, the level of a single state or defined region — usually to share information about any and all of topics, events, and operations of interest to that state or region. Examples include New Jersey Law Enforcement ISE and the ISE that connects state and regional fusion centers.
Mission Interest ISEs
Some ISEs are established solely to serve a narrow, but enduring, mission or functional community of interest (COI). It is this restricted, “functional” scope that distinguishes them. Examples include ISEs established to exchange information between government (and government-affiliated) experts on topics such as geospatial sensing, cyber defense, critical infrastructure protection, etc.
Tactical ISEs
Some ISEs are intended to be transitory, designed to serve only a specific tactical operation or series of operations, upon the conclusion of which the ISE is effectively dissolved. It is their relatively small scale and short duration that sets such ISEs them apart. Such ISEs are usually established by law enforcement or the military.
The ICIF: Providing a Common Thread Across Each Perspective
While each perspective above is somewhat unique in its goals and requirements, the ICIF provides value for each use case. Here’s why.
First, in each case, the ICIF helps to define behavioral norms at the “edges” of the environment, where participants’ systems and networks connect to each other. It introduces and enforces standards for organizational behavior in areas such as interoperability, security, privacy, and identity This characteristic of the ICIF brings tremendous value to any type of ISE, whether that ISE includes 2,000 participants or just two participants.
Second, while the ICIF creates logical structure around behaviors and capabilities at the “edges”, it does not impose changes to ISE participants’ internal legacy infrastructure. It therefore allows for tremendous flexibility in implementation. Agencies can leverage the ICIF within their internal infrastructure, if they so desire, for greater agility in responding to their current and future mission needs. But such “deep” adoption of the ICIF is optional. In practice, an agency can embrace the ICIF to whatever degree is practical in accordance with its goals.
Third, the ICIF can serve as a unifying and guiding construct that enables tactical needs to be met in a manner that also serves long-term strategic objectives, as indicated by the diagram below. In other words, since the ICIF fosters common organizational norms of behavior, as well as a standard language for expressing those behaviors, ICIF-related investments made by an agency for the purpose of participating in one ICIF-based ISE are likely to be highly reusable as part of future efforts within other ICIF-based ISEs.
ICIF Perspectives
[previous] [next]